I'm proud to announce a new program of mine called AORTA which stands for Another Onion Router Transproxy Application. AORTA is a small Linux utility that transparently routes all TCP and DNS traffic from a program under its control through the Tor network.
Transparent means that a program does not need to have a special Tor configuration, you simply let AORTA start the program and it will magically start using the Tor network.
Usage is as follows:
aorta [aorta parameters] [program] [program parameters]
possible (optional) aorta parameters are:
-t enable terminal output (for programs like wget, w3m etc.)
-c DO NOT CHECK if Tor handles all Internet traffic
-a DO NOT CHECK if the targeted program is already active
Note: ONLY use a DO NOT CHECK option if you are *very sure* that the check is
indeed not needed.
Examples:
aorta firefox https://check.torproject.org
aorta chromium expyuzz4wqqyqhjn.onion
aorta -t w3m expyuzz4wqqyqhjn.onion
aorta -t git clone http://dccbbv6cooddgcrq.onion/tor.git
aorta bash
AORTA makes use of some newer kernel and firewall technologies. Your system should have:
1. A Linux kernel with a version number greater than 3.14. You can check this with the following command:
uname -a
Which reports on my system:
---------------------------
Linux jessie 4.9.0-4-amd64 #1 SMP Debian 4.9.51-1 (2017-09-28) x86_64 GNU/Linux
My kernel version is 4.9 and meets this requirement.
2. An iptables version with cgroup support. This can be checked as follows:
/sbin/iptables -m cgroup -h | grep cgroup
On my system this results in:
-----------------------------
cgroup: Could not determine whether revision 1 is supported, assuming it is.
cgroup match options:
[!] --path path Recursively match path relative to cgroup2 root
[!] --cgroup classid Match cgroup classid, can't be used with --path
The cgroup match options in the output indicate that cgroup support is available.
The Tor network hides your IP address, but it does not anonymize the contents of your network traffic. AORTA can magically route all network traffic from a program through the Tor network, but AORTA too can not anonymize the contents of your network traffic.
If you use a program that generates network traffic that contains information that can identify you, then that traffic can be used to identify you once it leaves the Tor network. I can imagine that some of you are a little bit confused, what do I mean? Let me give you two examples:
-
If your email client program connects unencrypted to an email server over the Tor network, then all your email traffic, including your user name and password, can be read at the Tor exit node.
-
Network traffic from web browsers contain a lot of identifying information. In most cases this information does not identify you directly, but it can still be used to track you down. Take for example a user ID stored in a cookie: if your browser at one moment in time have sended that cookie without using Tor, your real IP address can be guessed - from all recorded IP addresses seen sending the cookie, it's the one that not belongs to a Tor exit node.
The Tor project has made a special version of Firefox called Tor Browser which minimizes the sending of user identifying information. You should use Tor Browser if exposing your identity is dangerous to you. If you just don't like to be monitored by your friendly government agency or ISP, it's fine to use a normal web browser in combination with AORTA. Note however that Tor Browser has its own Tor connection and should not be started by AORTA.
Installation of AORTA involves the following steps:
-
Download and extract AORTA.
You can download AORTA by clicking this link which takes you to the latests version of AORTA on the downloads page. Let's assume you downloaded version 1.1 of AORTA, then you can extract it as follows:
tar xfvz aorta-1.1.tar.gz
-
Go to the extracted aorta directory and compile the source code.
cd aorta-1.1
gcc -Wall -o aorta aorta.c
This should result in an executable named aorta. If compilation does not work then you probably have no gcc compiler/environment installed. On Debian and Debian based systems like Ubuntu and Linux Mint the build-essential package contains the missing tools.
-
Execute the following commands as root:
cp aorta /usr/local/bin/aorta
chown root:root /usr/local/bin/aorta
chmod u+s /usr/local/bin/aorta
-
Change the configuration of the local Tor daemon.
The configuration file /etc/tor/torrc should contain the following lines:
VirtualAddrNetworkIPv4 10.192.0.0/10
AutomapHostsOnResolve 1
TransPort 9040
DNSPort 9041
You can add these lines at the end of the file. After you changed the Tor configuration the Tor daemon must be restarted:
-
Test if aorta is working.
You now should have a working aorta program. You can test it by executing the following command:
aorta -t curl https://check.torproject.org/api/ip
on my system this results in the following output:
--------------------------------------------------
TESTING if Tor handles all Internet traffic
...Resolving - expyuzz4wqqyqhjn.onion
...IP address - 10.229.18.254
...Connecting - Done!
...Sending request - Done!
...Getting response - Done!
PASSED Tor connection test
RUNNING curl https://check.torproject.org/api/ip
{"IsTor":true,"IP":"137.74.73.179"}
AORTA CLOSED ...
AORTA works correctly if the output contains "IsTor": true
AORTA can only do its magic if the program it starts is under its control. In technical terms: the program must be a child process of the aorta program.
Some programs escape aorta's control if the program is already running. These programs detect at start if there is a running instance of the program. If so, they do not start a new program but instead clone the running program. This clone is a child of the running program and therefore not under the control of aorta. The clone will not use the Tor network.
AORTA checks if there is a running instance of the program you want to start and warns you about the possible problem as follows:
aorta firefox
TESTING if Tor handles all Internet traffic
...Resolving - expyuzz4wqqyqhjn.onion
...IP address - 10.229.18.254
...Connecting - Done!
...Sending request - Done!
...Getting response - Done!
PASSED Tor connection test
WARNING
The program you want to start is already running. Some programs will clone
a running program. If so, this cloned program will NOT USE THE Tor NETWORK.
You can detect this behavior as follows:
- AORTA exits after the program is started
- The title bar of Firefox/Chrome does not show (on AORTA).
- https://check.torproject.org reports: You are not using Tor.
Do you want to continue (y/N)?
It is not wise to ignore this warning. If you do you should be pretty sure that the warning is false.
IMPORTANT For AORTA it is not always possible to detect if a program is already running. On Linux it is quite simple to create a link to a program with a completely different name. It is also quite common to let a script start the actual program. In that case the script name can be different from the program name.
During testing of AORTA the following problems were detected:
-
Firefox cannot access onion sites when running under AORTA.
By default Firefox blocks onion addresses. Changing this behavior involves the following steps:
- type about:config in the address bar and press enter.
- promise you will be careful!
- type dns in the search field on top of the page.
- change the network.dns.blockDotOnion setting to false.
-
AORTA fails to run non-terminal programs.
This problem was detected when running aorta on an ArchLinux system. It turned out that the X-server configuration of ArchLinux does not allow access from a remote system.
Just before AORTA starts a program it changes the host name (only for that program). A new host name can be handy because:
- When a shell is started by aorta, the host name will be part of its prompt
- X11 programs like Firefox and Chromium show it on their title bars.
So, a new host name can give a visual indication that a program is using the Tor network. But on an ArchLinux system the new host name makes the X-server think it is accessed from another system, which is not allowed by the configuration.
There are 2 solutions for this problem:
-
Comment-out or remove the new_hostname function in aorta.c (it's in the main function). You have to compile and install aorta again if you do this.
-
Make the X-server configuration less restrictive by running the command:
xhost +local:
This command won't survive a restart. For this you have to add it
to .xinitrc, just before the GUI is started.
I hope you enjoy my little program. Don't hesitate to report problems that you encounter.
Comments: 4
Lately I started running Tor on an OpenWrt router (see my previous article). This turned out to be quite a nice experience - Tor on the router has many benefits for Tor-network clients.
Moving Tor from your computer(s) to the router can change the Tor-network landscape. Routers have the most direct Internet connection and they run 24/7. This opens up the opportunity to donate bandwidth to the Tor-network, and while a single router can probably donate little bandwidth there's strength in numbers. In this article I will do some calculations that will hopefully convince you that the potential bandwidth contribution of routers running Tor-firmware is very interesting.
Can many low-bandwidth client routers make a significant contribution to the bandwidth of the Tor-network? To answer this question we must first look at the current bandwidth of the network, and how it is used. Thanks to the Tor metrics project we have data about the bandwidth of the Tor network:

In this graph the bandwidth is the sum of both incoming and outgoing traffic of all relays in the Tor-network. The advertised bandwidth is the sum of the bandwidth each relay claims it can provide. The bandwidth history is the sum of the bandwidth that is reported to have been used.
I think we all agree that the graph shows some impressive numbers. But without understanding the way the Tor-network works you might get the wrong picture. From the clients perspective the bandwidth history is not ~75 Gbit/s but ~12 GBit/s. Why is that? To understand this we need to look at the bandwidth a single client uses:
Client --> OR1 --> OR2 --> OR3 --> Server
One client uses the bandwidth of three onion routers, and for each onion router the client uses both upload and download bandwidth. For a client to upload 1 MB of data, roughly 6 MB of Tor-network bandwidth is needed.
In order to get an idea of the average bandwidth a Tor router can contribute to the Tor-network I use data from Akamai. As you probably know, Akamai is a firm that operates a huge content delivery network. Every quarter they publish a lengthy report with metrics on the observed download speed in different countries. This report contains two metrics of interest: Average connection speed, and Average peak connection speed.
Most publications about the speed of the Internet only mention the average connection speed, which does not represent the connection speed of the users. This has to do with the way Akamai measures it. For Akamai, the average connection speed is the average speed of a http file download. If you request a web-page however, many parallel downloads are taking place which all share the same connection. So, the average speed in the Akamai report is only a fraction of the real speed of the Internet connection. The average peak connection speed only uses the maximum observed download speed of an IP address. This is most likely the speed with no parallel downloads, and thus best represents the speed of the Internet connection.
To get a good idea about the bandwidth of Tor-network users we cannot simply use the average peak Internet connection speed of 32 Mbit/s mentioned on the Akamai website. The Tor metrics show that most Tor users are living in relatively rich countries with good Internet speeds. Therefore I decided to calculate the bandwidth using the data of the 10 counties with the most Tor users.
Top 10 countries: 2016-02-11 to 2016-05-11
Country Mean daily users Avg download speed(Mbit/s)
=================================================
United States 364015 (19.38 %) 61.5
Russia 214670 (11.43 %) 60.0
Germany 187220 (9.97 %) 51.3
France 112798 (6.01 %) 43.2
United Kingdom 84199 (4.48 %) 56.8
Italy 54166 (2.88 %) 32.0
Spain 53045 (2.82 %) 59.9
Brazil 49302 (2.62 %) 30.3
Japan 47675 (2.54 %) 82.9
Canada 42031 (2.24 %) 54.9
=================================================
1209121 (64.37 %) 55.6 (weighted)
Weighted Avg download speed:
364015 * 61.5
+ 214670 * 60.0
+ 187220 * 51.3
+ 112798 * 43.2
+ 84199 * 56.8
+ 54166 * 32.0
+ 53045 * 59.9
+ 49302 * 30.3
+ 47675 * 82.9
+ 42031 * 54.9
=============
67191202.8 / 1209121 = 55.6 Mbit/s
Mean daily users all countries: 1209121 / 0.6437 = 18800000
As you can see, taking the global distribution of Tor users into account leads to a much higher average download speed. What I find interesting is that this speed is rapidly improving as the next graph shows:
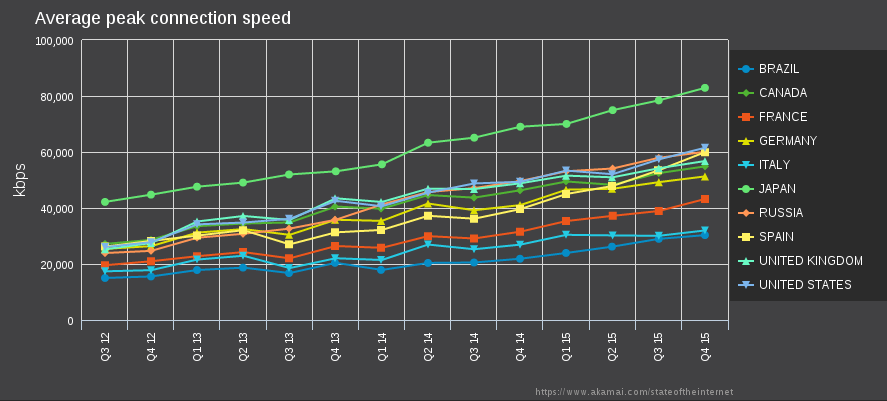
(Graph made with: Akamai data visualization)
Until now I have only talked about the download speed. What about the upload speed? Most Internet connections are asymmetric having an upload speed which is typically 1/10 of the download speed. This upload speed becomes the limiting factor for the bandwidth a Tor router can contribute to the Tor-network. On average I think one Tor router can contribute 5 Mbit/s in both directions, a total of 10 Mbit/s.
There's one question left to answer: does this bandwidth contribution hurts the normal Internet use of the user? Well, not for downloading because it only uses 1/10 of the download speed. For uploading I looked at my Internet statistics: My peak average daily upload speed was 60 Kbit/s. Many days had a much lower daily average. I think that users who are not doing much uploading will probably not notice the sharing of the upload bandwidth.
Now we have an idea about the average bandwidth contribution of a single Tor router we can start some calculations.
First: How many Tor routers are needed to provide the same advertised bandwidth of the current Tor-network?
170000 Mbit/s / 10 Mbit/s = 17000 routers
17000/1880000 = 0.9% of the Tor users
Second: How many Tor routers are needed to provide the same observed bandwidth of the current Tor-network?
75000 Mbit/s / 10 Mbit/s = 7500 routers
7500/1880000 = 0.4% of the Tor users
Wow, it only takes a very small percentage of Tor users donating bandwidth to provide the same bandwidth that the Tor-network has today. Even better, if the number of Tor users increase so does the donated bandwidth.
Of course, at the moment there is no "Tor router", and the Tor software is not ready to make use of bandwidth donated by clients. I hope this article convinces you that having an official "Tor router" would not only benefit the Tor users, but it will also create new opportunities to expand and strengthen the Tor-network. What do you think?
Comments: 0
In my previous article I shared my thoughts on running Tor on the router. I described an ideal Tor router configuration and argued that having Tor on the router benefits both security and usability.
This article is about that ideal Tor router configuration. How did I configure my router, and why did I choose the configuration? The interesting part is that it really is “just configuration”. No programming involved. Even more interesting, it's easy too!
All the configuration is for a GL-AR150 portable router. A very cheap router ($25 on Amazon) that has special Tor firmware that you can install after you bought the device. To be honest, when I bought the device I did not expect much of it. It just seemed too cheap to be more than a toy. Boy was I wrong - after playing with it for some time I realized that it is the most powerful router I have ever owned.
So, what are the specs? (more details here)
Chip: Atheros 9331 Soc at 400MHz
OS: OpenWrt Chaos Calmer 15.05
RAM: 64 MB
ROM: 16 MB
USB: 1*USB 2.0
Ethernet: 2 * 100 Mbps
Wireless: 802.11b/g/n (150 Mbps)
In the default configuration one of the Ethernet ports (eth0) must be connected to the Internet modem (WAN). The second Ethernet port (eth1) and the wireless interface are used for the LAN. Because I was interested in the Tor firmware I have not played much with the factory configuration.
After installing the manufacturers Tor firmware the router has the following configuration:
Wired:
eth0 - Configured as WAN interface
eth1 - Transparently routes all LAN traffic through the Tor-network
Wireless:
SSID OpenWrt - Acts as a normal LAN wifi interface (no Tor routing)
SSID tor - Transparently routes all LAN traffic through the Tor-network.
To prevent repeating myself I will discus the details of this configuration when I compare it with my own configuration. Let's get started:
My Tor configuration is as follows:
Wired:
eth0 - Used as WAN interface
eth1 - Limits Internet access to programs using the Tor SOCKS interface
Wireless:
SSID tor_off - Normal, unrestricted LAN wifi interface
SSID tor_medium - Transparently routes all LAN traffic through the Tor-network.
SSID tor_max - Limits Internet access to programs using the Tor SOCKS interface.
As you can see I configured an extra way to connect to the Internet. Eth1 and SSID tor_max only allow programs that are configured to use the Tor SOCKS interface to connect to the Internet. Why have I done this? The reason is that the transparent Tor interface does not offer the best possible privacy protection. With transparent routing many chatty background services are also routed through Tor and their invisible traffic can de-anonymize the user. An example is a mail program that checks the mail every 10 minutes over an unencrypted connection.
The SOCKS-only interfaces do not have a route to the WAN interface, so it's not possible to connect to the Internet directly. To make connected computers aware of this, gateway and name server addresses are not set by the router's DHCP server. Eth1 and the tor_max AP are part of a bridged network. Computers connected to eth1 can access computers connected to the tor_max AP (and vice versa).
One of the things I did not like of the original configuration was the fact that the transparent Tor routing blindly forwarded all TCP traffic to the Tor daemon. This prevented accessing the router's UI and SSH server. My setup only forwards non-local TCP traffic so that the UI and SSH server can always be reached.
I think we all know that the Internet can be dangerous with regard to privacy and security. Spy-ware, Trojans etc. all need the Internet to function. So why do we allow our computers to be connected to the Internet all the time? It would be better if we could choose which programs can use the Internet and when. With this in mind I came to the following wired network configuration:
computer(s) – network switch – eth1[GL-AR150]eth0 – Cable modem – The Internet
As said before, the eth1 interface has no Internet connection. This is not as inconvenient as you might think because my web-browser can still connect to the Internet by using the Tor SOCKS proxy provided by the router.
What if a computer needs an Internet connection? Then there are two options:
-
First I can plug-in a handy USB wifi adapter and connect to the tor_off access point. The DHCP server on this access point will set the gateway and name server addresses making it possible to use the Internet. If you have an integrated wifi adapter (laptops) things are of course simpler - configure the adapter to use the tor_off access point by default, and only switch on wifi if you need an Internet connection.
-
The second option would be to use the router's UI to reconfigure eth1 into a normal forwarding configuration. This involves changing the network, DHCP and firewall settings and restarting these services. The disadvantage of this solution is that all computers connected to the switch get full Internet access too.
I did not like the second option. Making it safe would involve MAC filtering so that only one computer at a time gets connected. This can be done but it is complicated. I like simple, so I did not even try to implement the second option.
One big advantage of my setup is that it's now safe to use devices that are designed to spy on you (I mean Android devices of course). I remember that I was quite shocked when I first browsed the Google Play store. Almost all the apps were spy-ware! A simple flashlight app would need access to your contacts, location, history, birth-certificate etc. On my Android tablet I read a lot of books and I am worried that the book reader apps would report on everything I read. Something like: Rob is reading "The hitchhikers guide to the galaxy" and made a note on page 42 about the importance of towels. These worries made me decide to disable wifi on my tablet which is of course a major PITA. With my new setup I connect my tablet to the tor_max access point. This gives apps on the tablet access to to my internal network, but not to the Internet. They cannot send their reports or download helpful adds! Also, by configuring Firefox to use the SOCKS proxy, I can use my tablet for web surfing.
Being a programmer I could not resist to explore how the GL-AR150 could be programmed. This turned out to be quite a disappointment. It was way too easy! No kidding, the OpenWrt people did an excellent job, programming an OpenWrt device is fun!
I enjoyed myself making a small status page (example here) similar to the home page of the original GL-AR150 firmware. The difference is that there is no need to log in to see the router's status. It also displays much faster.
You can access the new status page by surfing to /torbox on the routers IP address:
http://192.168.100.1/torbox (eth1 and tor_max)
http://172.16.1.1/torbox (tor_off)
http://172.16.50.1/torbox (tor_medium)
Note: torbox is just an internal name I use for my router. I do not intend to release a project/product under the same name.
Installing the status page does not replace the web-UI of the manufacturer. You can still reach it by surfing to the bare IP-address. Remember however that the web-UI of the manufacturer was designed for the manufacturer's configuration. It contains some hard-coded values and is incompatible with my configuration. Choose the more generic LUCI web-UI from the manufacturer's UI if you want to change a setting (note: I find it easier to edit the files in the etc/config/ directory)
I hope you like my configuration enough to give it a try. If you do, remember that I can give you no warranties. Use my configuration at your own risk. As far as I know it's not possible to brick your device. It should always be possible to restore the factory configuration by pressing the reset button for 10 seconds.
My configuration requires the manufacturer's Tor firmware (version 1.3 at the time of writing). You can download and install this firmware by following the instructions in this article: new-tor-firmware-for-gl-ar150-and-gl-inet6416. The firmware link in the article is not the latest version. You can download the latest version at http://www.gl-inet.com/firmware/ar150/tor/
After you installed the Tor firmware you must use its UI to set the board-name (use torbox), root password and timezone of the router. You can access the router's UI by connecting to http://192.168.8.1 (if you are asked for a password use goodlife)
Before installing my configuration it's important to check if the manufacturers Tor firmware works. If not, my configuration will not function too.
Installing the configuration is a simple copy-paste process. Replacing some files and adding others. The file containing the configuration has the same directory structure as the router and can be downloaded here. Inside the archive you find the following directories and files:
Files for changing the network configuration:
etc/config/dhcp
etc/config/firewall
etc/config/network
etc/config/wireless
A new Tor configuration file:
Files for adding an extra status-page:
etc/config/uhttpd
www/torbox.css
www/torbox.lua
www/bumblebee.jpg
After you unpacked the archive you might want to change the wireless passwords in etc/config/wireless. It's best to use a different password for the tor_max interface because this interface has access to your LAN computers/devices. If you want you can also change the ssid's. Do not change the other options!
The best way to copy-paste the files is by making a SFTP connection to the router. When I tried this, it did not work. The dropbear SSH server of the router did not support SFTP. I had to install the openssh-sftp-package to get SFTP working:
ssh root@192.168.8.1
opkg update
opkg install openssh-sftp-server
It is also possible to use the LUCI web-UI of the router to install the package. You can access the web-UI by connection to the OpenWrt wifi access point and then surf to http://192.168.8.1/
On Debian you can now use Nautilus's “File->Connect to server” to establish a SSH connection to the router (use IP address 192.168.8.1). After copy-pasting you have to restart the router for the configuration to take effect. The configuration changes IP addresses and SSID's to the following:
eth1: IP 192.168.100.1 network 192.168.100.0/24
SSID tor_off: IP 172.16.1.1 network 172.16.1.0/24
SSID tor_medium: IP 172.16.50.1 network 172.16.50.0/24
SSID tor_max: IP 192.168.100.1 network 192.168.100.0/24
If you did not change the password in the wireless configuration file, the password for the wifi access points is goodlife.
If you like my setup, I hope you will give it a try. The hardware is very cheap, so for most of you buying the device needed will not be a problem. Here are some links to shops:
The GL-iNet webshop
GL-AR150 on Amazon
Same with external antenna
If you are living in The Netherlands and have no credit-card, you can buy one from Deal Extreme where you can pay with iDeal.
GL-AR150 on Deal Extreme
Comments: 0
I recently came across a small travel-router that claimed to provide transparent access to the Tor-network. Just make a wifi connection to its Tor access point and all the TCP and DNS traffic is routed through the Tor-network. For a price of only $25 I could not resist and bought one. Over the last month I have been playing with the device and... it worked flawlessly, it was fun!
So, running the Tor software on cheap router hardware works, but is it a good idea? I believe it is. In this article I will argue that having Tor on the router benefits both security and usability. It opens up new possibilities for expanding the Tor-network and can provide a much needed source of income for the Tor-project.
In this article I will refer to an ideal Tor router. This router will provide 3 wifi access points (AP) with the following SSID's:
- TorOff : This AP does not route through the Tor-network.
- TorTransparent: Provides a transparent Tor proxy.
- TorSocks: Provides access to the Tor SOCKS interface of the router's Tor daemon. Except for DHCP, all other traffic is blocked.
The software running on the router is based on OpenWRT and signed by the Tor-project. It should not be possible to add additional software.
I strongly believe that running the Tor daemon on the router improves security. This is why:
-
If a user connects to the TorSocks AP instead of a local Tor daemon, it becomes impossible to bypass the Tor-network. Software that is not configured to use Tor will not be able to use the Internet.
-
The Tor daemon on the router runs in a much more secure environment. On the router just a few carefully selected processes are running. Processes that are controlled by the Tor-project that signed the firmware. Compare this with the Windows environment where there is no control. If Microsoft wants to replace your Tor daemon with its own version it can do so.
-
While using the TorSocks AP benefits security, the story for the TorTransparent AP is more complicated. The transparent AP routes all TCP and DNS traffic through the Tor-network. This includes traffic from many chatty background services which may leak information that can de-anonymize the user. An example is a mail program that checks the mail every 10 minutes over an unencrypted connection. To protect users who are unaware of this background traffic I think the transparent AP should only allow HTTP and HTTPS by default.
For strong anonymity the user should use special privacy enhanced software like the Tor browser in combination with the TorSocks AP.
Having the Tor daemon running on the router improves usability in the following ways:
- Better maintainability.
- Easier client configuration.
- Better client support.
Running Tor on the router means that Tor does not have to be configured and maintained on every device in ones home. Because the router uses an OS that is controlled by the Tor project, it can automatically update the Tor software (improves security too).
No special client configuration is needed if the TorTransparent AP is used. This means that programs that are not Tor-aware can use the Tor-network to gain a privacy benefit. Of course, it must be made clear to the user that the transparent AP does not provide the best possible privacy protection. For the best privacy protection the user should use the TorSocks AP in combination with privacy enhanced software like Tor-browser.
Playing with Tor router hardware convinced me that its time has come. It can improve both security and usability for the users of the Tor-network. But what can it do for the Tor-project? I think the Tor-project can benefit in the following areas:
- Resistance against parties that can influence or even shutdown the Tor-network.
- A source of independent funding
- New possibilities to strengthen the network and improve the anonymity of the users.
The first point has probably surprised you. Which parties am I talking about? How can they influence or even shutdown the Tor-network? The answers are simple. Most Tor software runs on an OS that is under the control of Google (Android), Microsoft or Apple. These companies have the power to remove or modify the Tor software. Will they do this? Probably not, but remember that risk = chance * effect. The effect of removed or modified Tor software is simply not acceptable which makes it a high risk. Currently the Tor-project has no defense against a hostile act of the OS manufacturers.
One of the weak points of the Tor-project is its funding. Roughly 75 percent comes from grants from US government related institutions. These grants are not stable income, and also make people wonder if the Tor-project is not secretly working for the US. The Tor-project needs to diversify its funding.
I am pretty sure that developing Tor router firmware can become a stable source of income for the Tor-project. Why? Because a there is already a company that sells Tor router hardware. The story of this company is very interesting. They misled their customers about the hardware, claiming it was developed in-house while instead they used of-the-shelf hardware from China. For this their crowdfunding campaign on Kickstarter was suspended. Later analysis of their software revealed some serious security flaws. All this did not finish the company, today they are selling different versions of their AnonaBox for prices ranging from $80 to $120 (of which a generous $1 is donated to the Tor-project!)
The last benefit for the Tor-project that I want to mention are the possibilities to strengthen the network. Think about it; each Tor router adds hardware to the Tor-network that runs 24/7. Hardware that is under the control of the Tor-project. What can you do with this hardware? I don't have all the answers here. In the past I have showed that you can use a router as a Tor-bridge with some simple WAN-NAT iptables rules. Another interesting possibility would be to integrate Tor-browser into the router and access it using a remote desktop connection. This may not be possible today, but it will certainly be possible tomorrow.
I had (and have) a lot of fun playing with my Tor router hardware. Here are some links for those who are interested:
First my device. I bought a GL-Inet GL-AR150
GL-AR150 Specs
GL-AR150 Tor firmware:
You can buy it from:
GL-AR150 on Amazon
If you are living in The Netherlands and have no creditcard, you can buy one from deal extreme where you can pay with iDeal.
GL-AR150 on Deal Extreme
Note: Hardware with a much faster processor and twice the amount of RAM is coming soon (two weeks?):
GL-MT300A Specs
Comments: 0
